Fraud Prevention
Fraud Prevention
Prevents identity theft and fraudulent transactions
CIAM vertical comprising Fraud Analysis and Device Fingerprint products. It detects fraud in multichannel mode, using Mpredictive system to create smart profiles and alert when a transaction falls outside the usual parameters. In addition, it identifies the devices of users connecting to an online system by collecting technical data and properties.
CIAM vertical comprising Fraud Analysis and Device Fingerprint products. It detects fraud in multichannel mode, using Mpredictive system to create smart profiles and alert when a transaction falls outside the usual parameters. In addition, it identifies the devices of users connecting to an online system by collecting technical data and properties.
.png)
Real-time analysis
Transaction description
Define rules at runtime
Learn more about the benefits of
Fraud Prevention
Unique behavior profile
Analize client behavior and generate a unified profile
Reduce risk
Optimize operations with automatic transaction approval — increase acceptance rates by avoiding false positives
.png?height=60&name=Frame%203512%20(11).png)
Risk-based security
Implement risk-based security by integrating with authentication and device analysis solutions
.png?height=60&name=Frame%203512%20(6).png)
Protect your business
Avoid fines, sanctions, financial losses, ineligibility to manage certain products, and the revocation of licenses needed to operate in the financial market

Safeguard your reputation
Secure and comfortable online experiences that gain the trust of current and future clients
.png?height=60&name=Frame%203513%20(1).png)
Robust authentication
Alert to suspicious transactions, both passive and active, through a robust authentication process personalized to each user profile, while blocking those that may be a threat to your business

Fraud Prevention's features
Predictive system
Identify patterns and behaviors associated with high-risk users and transactions to trigger responses based on predictive analysis and transactional profiles
Rule-based engine
Predefined and personalized administration rules that trigger actions in real time
KYC
Create personalized lists and connect with blacklists, government sources, credit bureaus and identity data providers, even in regions that don’t have data sources available
User scoring
Generate a behavior-based user profile and assign risk points that alert to possible suspicious activity
Geolocation
Select transactional safe zones according to normal user behavior
Risk-based authentication
Evaluate risk based on frequent user events, and select the level of authentication required
User Experience
Makes it easier for risk and fraud analysts to deal with suspicious transactions and allows action on alerts in real time.
Intuitive interface
Enable Risk Officers and Fraud Analysts to easily identify suspicious transactions and see alerts in real time
Reporting and analytics
Easily generate predefined and customizable reports including: suspicious activity reports, compliance reports, trade logs, and normative standardsWith VU's flexible
Fraud Prevention solution
you will have access to:
How does it work?
Smart User Profiles
We create smart user profiles by using big data techniques and analysis of transactional behavior including: user connectivity data, amounts, dates, frequency, and operation type. These fields can be personalized by the operator to generate web services compatible with those in use.
Rule-based Engine
We have a static and dynamic rule-based engine that we build based on how each user operates and the most common fraud events associated with the characteristics of each business.
Artificial Intelligence
Artificial intelligence and machine learning enable real-time data storage and processing to detect, alert to, and act on threats that put the security of platforms, systems, and applications at risk.
Smart User Profiles
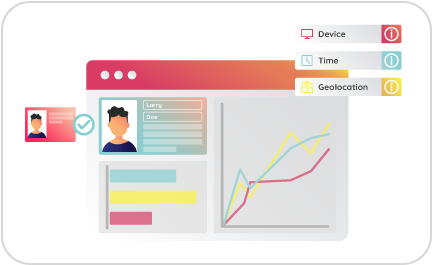
Smart User Profiles
We create smart user profiles by using big data techniques and analysis of transactional behavior including: user connectivity data, amounts, dates, frequency, and operation type. These fields can be personalized by the operator to generate web services compatible with those in use.
Rule-based Engine
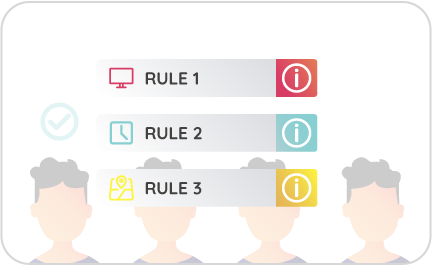
Rule-based Engine
We have a static and dynamic rule-based engine that we build based on how each user operates and the most common fraud events associated with the characteristics of each business.
Artificial Intelligence

Artificial Intelligence
Artificial intelligence and machine learning enable real-time data storage and processing to detect, alert to, and act on threats that put the security of platforms, systems, and applications at risk.
Learn more about
Fraud Prevention use cases
%20(1).png)
- One-click online payment.
- User scoring.
- Prevention of money laundering from transactions originating from illegal or unregulated sources
- Identification of mule accounts through banned lists, to which accounts suspected of being used for fraudulent maneuvers are added.