.webp?width=293&height=264&name=image_picker_2E118A6C-17AF-4C97-9A0C-35D3057246E3-2944-000001487714D85E%201%20(1).webp)
We facilitate the management of customer identities through our extensive cybersecurity platform.
Learn more about our solutions for identity protection and fraud prevention based on the behavior of each Online Persona.
Live the VU Experience











.webp)
Creation of secure and frictionless digital identity during the onboarding process.
CONTACT SALES.webp)

We prevent fraud and identity theft while complying with all applicable regulations.
CONTACT SALES%20(2).webp)
We respect the right of users to be forgotten – providing them the possibility to consolidate their identity, undertand what data has been collected, and control what is done with their data upon unsuscribing; guaranteeing privacy and confidentiality.
CONTACT SALES.webp?width=293&height=264&name=image_picker_2E118A6C-17AF-4C97-9A0C-35D3057246E3-2944-000001487714D85E%201%20(1).webp)
We facilitate the management of customer identities through our extensive cybersecurity platform.
Minimize investment by taking advantage of existing systems.
Allow users to securely login using the most modern apps on the market.
Save time, improve efficiency, and gradually enrich the available data on each user.
Make users happier with 100% autonomy: registration, login, authorizations, re-registration, and account recovery — all without human interaction.
Give users control over their consent, privacy, and preferences — while ensuring compliance with GDPR and similar laws and regulations.
Possibility of defining rules to discover multiple identities, consolidate them into a single one and get to know users better.
Preserve the digital identity of your users through our Authentication Management and Onboarding Management products.
TECHNICAL INFORMATION
Multi-Factor Authentication (MFA)
Passwordless
Biometrics and Continuous Authentication
Access Management
Social Login
Proof of Life
.gif)
Authenticate using multiple factors, channels, and devices.
Facilitate data entry through the use of magic links and secure push verification QRs that eliminate friction.

Adjust to user needs with real-time face, voice, digital fingerprint, palm, and behavior recognition.

Virtually integrate any device or user directory to improve system hardening.

Provides a unique form of security protection integrated with the social media channel.

Confirm life of users with technology that surpasses the accuracy of the human eye.
Protect companies from multi-million dollar losses and damage to their reputation.
Technical Information:
Automatic Anomaly Detection
Fraud Detection
User scoring
Geolocation Comparison
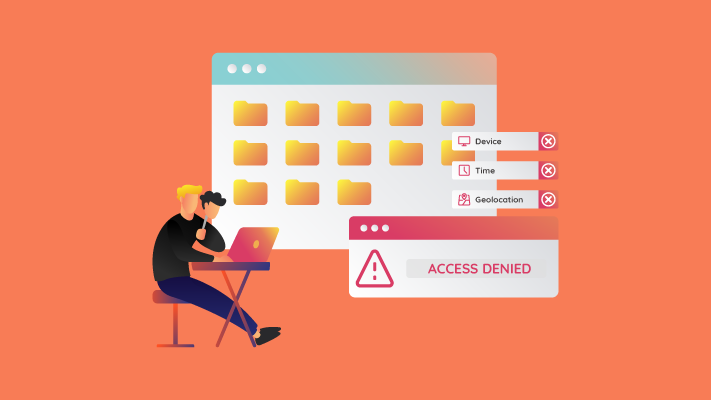
Compare geolocation, transactions, devices, and many more variables to avoid fraud.

Monitors the entire user cycle — from onboarding and conducting transactions to the login and logout of each user session.

Control how each user’s detail affects their scoring and constantly compares these values.
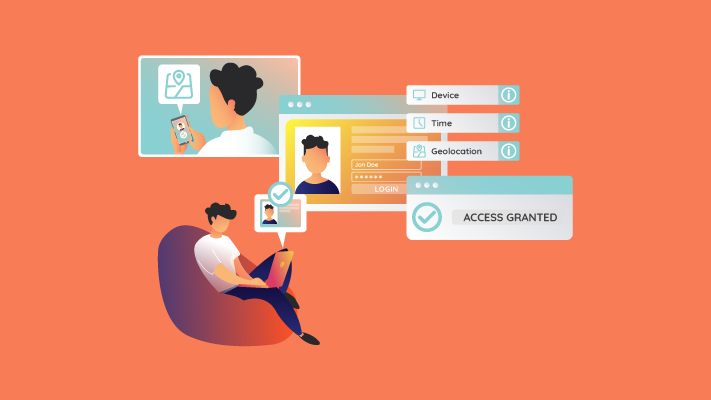
Set access limitations based on location, both geographic and functional.
Contact our Sales Team and discover our cybersecurity solutions.