Speeds up operations
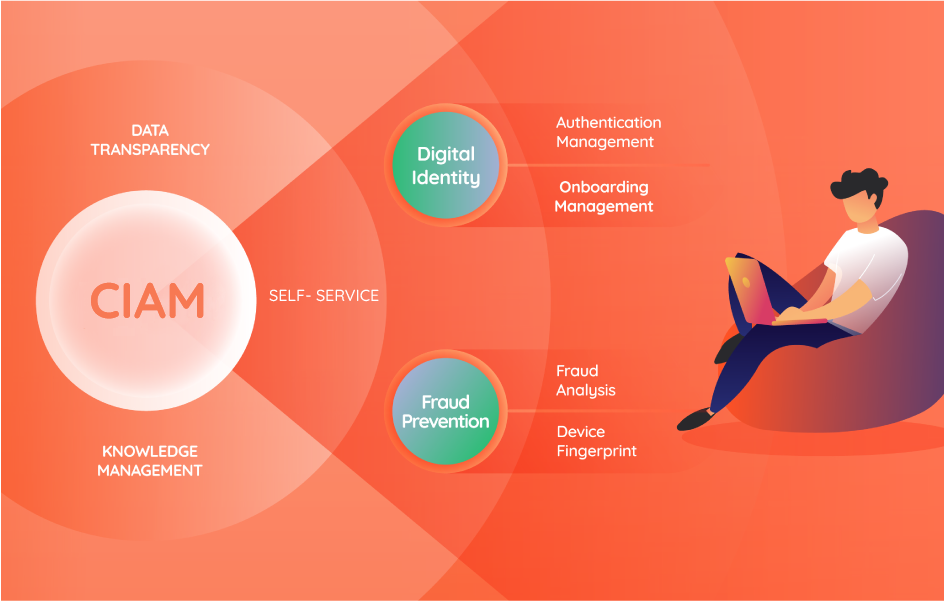
Comprehensive Unified Online Persona strategy orchestrating digital identity from registration, validation, proof of life, authentication, real-time behavior-based fraud detection and unsubscription.
Comprehensive Unified Online Persona strategy orchestrating digital identity from registration, validation, proof of life, authentication, real-time behavior-based fraud detection and unsubscription.
.png)

Implements a shared identity layer across all business units to allow centralized management and alignment with data protection regulations

Enables user identities to take on real meaning when interacting with different business units
.png?height=60&name=Frame%203513%20(1).png)
Eliminates friction, increases security, measures churn and fosters user commitment
.png?height=60&name=Frame%203512%20(4).png)
Encourages reconnection with customers.
-1.png?height=60&name=Frame%203512%20(2)-1.png)
Enables the possibility of having validated information from all users

Compiles business intelligence data
.png?height=60&name=Frame%203512%20(3).png)
Provides the ability to adapt to the complexities of each industry through dynamic digital identity management workflows.
.png?height=60&name=Frame%203513%20(2).png)
Allows the possibility of viewing all open sessions across any device

Includes a module to manage the right to be forgotten, and promotes the audited elimination of confidential information


Allows the definition of dynamic access roles for your your applications and APIs' end users.
Saves time, gains efficiency and gradually enriches the data available on each user.
For more independent users, with 100% autonomy regarding onboarding, login, authorizations, MFA management and account recovery without support teams' intervention.
Optimizes investment by leveraging the advantages of existing systems
Offers the possibility of defining rules to discover multiple identities, consolidate them into a single identity and get to know the users better.
Define access roles so that only those who have the corresponding access, can log into the application
Make the most out of our fraud detection engine to implement attribute-based access control
Incorporate and recognize usersn a way that adapts to every business, and provide identification services
Allows users to use a single identity between heterogeneous systems and log in through providers such as Facebook and LinkedIn under the concept of BYOID (Bring Your Own Identity)
Establish user sessions that can be securely and transparently reused within other internal, external, or cloud-based applications — eliminating the need to log in repeatedly
Control and audit who accesses your business’ resources by implementing security policies and authentication methods that will minimise risks
Provide complete administration services, that include both system configuration, its parameters, and user data
Enables applications to implement Single Logout seamlessly through Open ID Connect and SAML
Create rules focused on your business and apply machine learning techniques to prevent fraud through the detection of irregular user behaviour
Provide extensive activity logs, activity tracking, and integration with data lakes and advanced analytics reports
Simplifies access to its functions with software development kits, whose main features are a one-time password, biometric capture process and device fingerprint, based on JavaScript, and mobile development frameworks for Android and/or iOS, which facilitate integration with forms, applications and libraries for the use of devices

%20(1).png)